How To Become ISO 27001 Certified
Amid rapid technological advancements and digital reliance, safeguarding sensitive data stands as a paramount global concern. The ISO 27001 certification, established by the International Organization for Standardization (ISO), signifies a robust information security management system (ISMS). More than compliance, it fosters a culture of security, shielding against threats and building stakeholder confidence.
This guide offers a detailed journey to ISO 27001 certification, covering principles, implementation, and essential considerations. Navigating the stages equips organizations with insights to secure information assets and confidently stride towards ISO 27001 certification.
What is ISO 27001?
ISO 27001 is an internationally recognized standard that outlines the requirements for establishing, implementing, operating, monitoring, reviewing, maintaining, and improving an ISMS. The standard provides a systematic approach to managing sensitive information, identifying security risks, and implementing appropriate controls to mitigate those risks.
Importance of ISO 27001 Certification
In an interconnected world driven by digital innovation, the critical importance of information security cannot be overstated. The exponential growth of data, coupled with the ever-evolving sophistication of cyber threats, has led to an environment where organizations must prioritize safeguarding sensitive information like never before. Amidst this backdrop, ISO 27001 certification emerges as a beacon of trust and reliability, a testament to an organization's unwavering dedication to information security best practices.
ISO 27001 certification demonstrates a commitment to information security best practices. In an era where data breaches and cyber threats are commonplace, ISO 27001 offers a competitive edge by assuring clients, partners, and stakeholders that their data is safe.
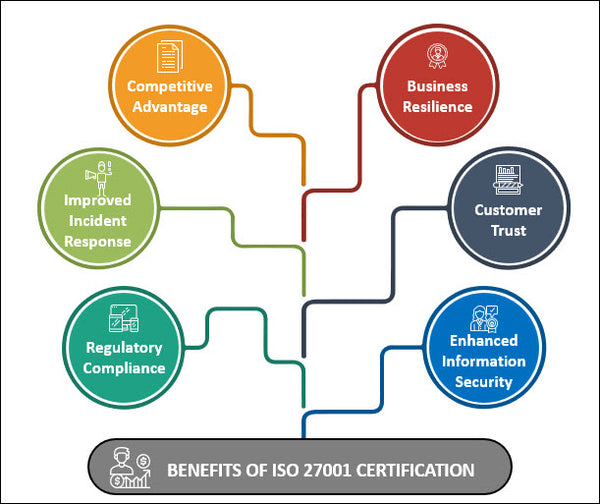
Benefits of ISO 27001 Certification
- Enhanced Information Security: ISO 27001 helps organizations identify and address vulnerabilities, reducing the risk of data breaches and unauthorized access.
- Regulatory Compliance: Many industries require compliance with specific data protection regulations. ISO 27001 assists in meeting these requirements.
- Customer Trust: ISO 27001 certification fosters trust and confidence among customers, showcasing a dedication to safeguarding their data.
- Improved Incident Response: A well-defined ISMS equips organizations to respond effectively to security incidents and minimize their impact.
- Business Resilience: ISO 27001 helps businesses maintain operations during and after security incidents, ensuring continuity.
- Competitive Advantage: ISO 27001 certification can provide a distinct competitive advantage, especially when bidding for contracts.
Key Steps to Achieve ISO 27001 Certification
- Conducting a Gap Analysis: Begin by assessing your current information security practices against the requirements of ISO 27001. Identify gaps and areas that need improvement.
- Establishing the ISMS Framework: Define the scope of your ISMS, appoint a management representative, and establish a cross-functional team to drive the certification process.
- Risk Assessment and Management: Conduct a thorough risk assessment to identify potential threats and vulnerabilities. Develop a risk treatment plan to prioritize and address these risks.
- Implementing Security Controls: Implement a set of controls based on the results of your risk assessment. These controls can include technical, physical, and administrative measures.
- Training and Awareness: Educate employees about their roles and responsibilities in maintaining information security. Foster a culture of security awareness throughout the organization.
- Performance Evaluation: Regularly monitor and measure the effectiveness of your ISMS. Use key performance indicators (KPIs) to track progress and identify areas for improvement.
- Internal Audit: Conduct internal audits to assess compliance with ISO 27001 requirements and the effectiveness of your ISMS.
- Management Review: Hold management reviews to evaluate the performance of the ISMS, identify opportunities for improvement, and allocate necessary resources.
- Corrective and Preventive Actions: Address non-conformities and take corrective actions to continuously improve the ISMS. Implement preventive measures to avoid recurrence.
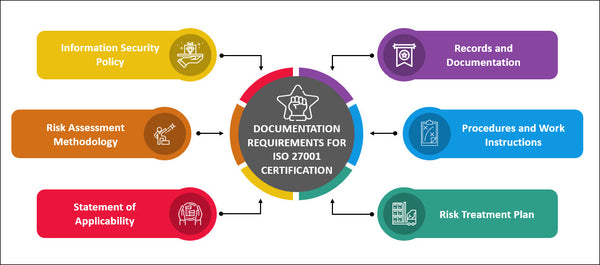
Documentation Requirements for ISO 27001 Certification
Documentation is a crucial aspect of ISO 27001 certification. Key documents include:
- Information Security Policy: Outlines the organization's commitment to information security.
- Risk Assessment Methodology: Describes how risks are assessed and prioritized.
- Statement of Applicability: Lists the security controls selected and their justifications.
- Risk Treatment Plan: Details how identified risks will be mitigated.
- Procedures and Work Instructions: Step-by-step guides for implementing security measures.
- Records and Documentation: Evidence of compliance and ISMS performance.
Engaging External Auditors
- Selection of Certification Body: Choose a reputable certification body accredited for ISO 27001 audits.
- Stage 1 Audit: The certification body performs an initial audit to evaluate the readiness of your ISMS.
- Stage 2 Audit: A comprehensive audit is conducted to assess the implementation and effectiveness of your ISMS.
- Certification Decision: Based on the audit results, the certification body decides whether to grant ISO 27001 certification.
- Surveillance Audits: Periodic surveillance audits ensure ongoing compliance and continuous improvement.
Staying Ahead in the Competitive Landscape: ISO 27001's Strategic Edge
In the cutthroat realm of modern business, gaining a competitive edge can often make the difference between success and obscurity. ISO 27001 certification emerges as a strategic asset that not only safeguards an organization's digital assets but also bestows a distinct competitive advantage.
Organizations that hold ISO 27001 certification send a resounding message to competitors: they are fortified against the perils of the digital age. This message can resonate with clients who are increasingly cautious about entrusting their data to entities that may be vulnerable to cyber threats. It is not uncommon for businesses seeking partnerships or services to prioritize ISO 27001-certified organizations, recognizing that the investment in information security reflects a broader commitment to excellence.
Furthermore, ISO 27001 certification can open doors to new opportunities. Many industries, particularly those handling sensitive information like healthcare, finance, and government, require adherence to specific data security standards. ISO 27001 provides a solid foundation for meeting these regulatory requirements, positioning certified organizations as viable candidates for contracts and collaborations that hinge on data security compliance.
Conclusion
ISO 27001 certification is a testament to an organization's commitment to information security and its ability to manage and protect valuable data assets. By following the comprehensive steps outlined in this guide, businesses can establish a robust ISMS, enhance their security posture, and earn the trust of stakeholders in an increasingly digital world. Embracing ISO 27001 is not only a means of compliance but also a strategic move toward sustainable success in today's data-driven landscape.



